Today’s security needs require them to have a high level of protection, especially when it comes to confidential data.
From payment methods like credit cards to personal information about consumers and business data, organizations that manage sensitive data need to ensure their security.
The Data Security Standard for the Payment Card Industry (PCI DSS) helps protect private information for cardholders. The Payment Card Industry Security Standards Council (PCI SSC) regulates the standard with guidelines to safeguard all cardholder information processing organizations.
See Also: How Can I Protect Stored Payment Cardholder Data?
Compliance with PCI DSS means adhering to minimum protection standards that consumers and financial institutions can ensure that the risk of loss from fraud and cyber-attacks is below acceptable limits.
See Also: Encryption Key Management Basics
The Hardware Security Module (HSM) is designed to provide a high degree of data protection to companies in various industries. For this article, we will discuss the role of HSMs in supporting PCI DSS compliance.
What is a Hardware Security Module (HSM)?
When processing transactions, all financial institutions rely heavily on cryptography, including endpoint authentication, secure communication, and card / PIN verification. For this, they depend on hardware security modules (HSMs). Hardware Security Modules (HSM) ensures confidentiality, integrity, availability of cryptographic keys, and any private data processed with a high degree of security.
Payment HSMs are highly responsible for the secure generation and storage of multiple cryptographic keys used in the payment ecosystem.
See Also: PCI DSS Compliant Key Management Lifecycles
One of the main problems arising from cryptography to protect sensitive data during storage and transmission is the complexity of managing the lifecycle of encryption keys. According to Kerckhoffs principle, the cryptographic system’s security must be in the protection of the key.
This switch should be managed as securely as possible since it is assumed that the potential attacker knows or can access all other parameters of the cryptographic system. If the key is compromised, the cryptographic system as a whole is compromised.
See Also: Advantages of Using a Credit Card Vault for PCI
In this context, using a Hardware Security Module (HSM) is one of the most recommended alternatives for handling cryptographic keys. HSM is also known as the Secure Application Module (SAM), the Hardware Encryption Device (HED), the Secure Cryptographic Device (SCD), or the Encryption Module.
It is a secure, tamper-resistant cryptographic processor specifically designed to protect the lifecycle of cryptographic keys and execute encryption and decryption routines. It provides a high-security level in terms of confidentiality, integrity, and availability of cryptographic keys and all sensitive data processed.
See Also: What Is Tokenization and How Does It Affect Your PCI Compliance?
HSM is a secure physical device; usually, an external device is plugged into a crypto processing computer. Crypto processors such as HSMs use data encryption algorithms to provide a higher level of security.
Payment HSMs can encrypt and decrypt data and manage digital keys. They are specially designed to protect confidential data.
Built with advanced hardware and extensively controlled and approved by third-party regulators, HSMs have tight access control. Hardware Security Modules (HSM) work similar to a credit card with a chip. The chip cannot be cracked, it happens within the authentication process, and cheating is almost impossible.
HSMs also serve as special cryptographic processing tools using cryptographic algorithms compliant with FIPS 140-2 security. HSMs ensure that cryptographic keys are valid for servers that process cardholder data.
Depending on the requirements, HSM devices can be classified into two types:
- General Purpose HSM: General Purpose HSM devices are typically used in PKI environments, HTTPS channels, DNSSEC, general sensitive data protection, and crypto-wallets. For example, we can list Public Key Cryptographic Standard (PKCS)#11, Microsoft Cryptographic Application Programming Interface (CAPI), Java Cryptography Architecture (JCA), Java Cryptography Extension (JCE), and others.
- Transaction and Payment HSM: HSM devices for Transaction and Payment typically provide cryptographic support for most card brands’ payment applications, and interconnect interfaces are generally more limited than general-use HSMs. Examples of usage areas include PIN usage, protection of electronic funds transfers (EFT), magnetic card production, personalization processes, data generation for EMV chips, performing payment transactions with debit and credit cards, and verifying cards, users, and crypto.
A payment HSM is a hardened hardware device, tamper-proof, used by the retail banking industry to provide a high level of protection to cryptographic keys and customer PINs used during the issuance of magnetic stripe and EMV chip cards, credit and debit card payment transactions, and their mobile app equivalents.
Payment HSMs typically provide native cryptographic support for all major card plan payment applications. They are subject to strict stand-alone hardware certification under global schemes such as FIPS 140-2, PCI HSM, and other additional regional security requirements such as MEPS in France and APCA in Australia.
Some of the common usage examples in the payment ecosystem are:
- PIN creation, management, and verification
- PIN block translation during network switching of ATM and POS transactions
- Card, user, and cryptogram verification during the payment process
- Providing payment credentials for payment cards and mobile applications
- Point-to-point encryption (P2PE) key management and secure data decryption
- Securely share keys with third parties to facilitate secure communication.
In addition to the locally distributed (on-premises) HSM model, many cloud service providers and HSM device manufacturers offer a Hardware Security Module as a Service or managed services. This new model has many benefits, including high scalability, availability, and additional integration options, over the conventional model.
Some examples of these services are:
Amazon Web Services: AWS Key Management Service (KMS) and AWS CloudHSM
- Microsoft Azure: Azure Reserved HSM and Azure Key Vault
- IBM Cloud Hardware Security Module
- Google Cloud Platform: Cloud HSM and Cloud Key Management Service
- Thales CipherTrust Cloud Key Manager
- Utimaco HSM-as-a-Service
- NCipher nShield-as-a-Service
For integration with PCI DSS environments, cloud HSM services may be useful but are not recommended for use in PCI PIN, PCI P2PE, or PCI 3DS environments. Exceptional encryption support and additional physical and additional physical and system lifecycle protection measures are required for these requirements.
How Do HSMs Work?
When a transaction is initiated at the vendor point of sale (POS) terminal, the transaction request is sent via a secure tunnel to the bank transaction location with protocols such as TLS v1.2. Keys are protected and used by HSM instead of keys used to verify customer card information stored on the bank’s servers. The bank server consults HSM to verify the encrypted data’s validity and either approves or declines the transaction.
The hardware security module (HSM) is a unique “trusted” network computer that performs cryptographic operations such as key management, key exchange, and encryption.
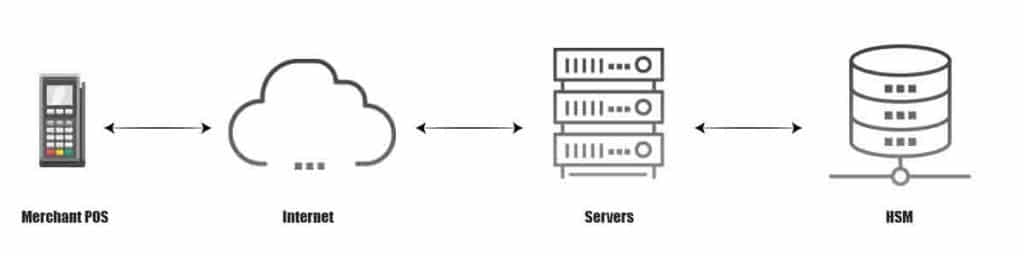
Cryptographic transactions must be performed in a secure environment. That’s why HSM hardware has been well tested and certified in special laboratories. It has a security-oriented operating system. It has restricted access through a network interface that is strictly controlled by internal laws. It actively hides and protects cryptographic materials.
A Hardware Security Module includes at least:
- Secret or private key
- A cryptographic engine
- Protection against key removal
Because the HSM contains both the key and the cryptographic engine, the sensitive secret key never needs to abandon the HSM restriction. Only data that needs to be encrypted or decrypted enters and exits the HSM. Because the private key never leaves the HSM, it cannot be accessed remotely by design.
What are the PCI DSS and HSM Requirements?
PCI DSS requirement 3.6.2, including secure cryptographic key storage, allows systems to be deployed to protect encryption keys used to encrypt cardholder-related data. Storing keys in unsafe locations can make a company vulnerable to cyberattacks.
Key encryption will have an additional layer of security. The dual control requirement guarantees confidence in the integrity of the switches when working with the HSM. HSMs that comply with FIPS 140-2 security level 3 and above will meet any PCI DSS requirements.
One of the key methods used to encrypt transaction data relating to payment cards is cryptography. Therefore, most of the controls in the PCI SSC standards (PCI DSS, PCI PIN, PCI P2PE, PCI 3DS, PCI Card Generation, etc.) require proper management of encryption keys and, in some cases, the use of specific HSMs and certificates.
To handle encryption keys, the PCI DSS standard does not require the use of an HSM computer. However, using HSM simplifies the following PCI DSS requirement processes:
- Secure key storage (PCI DSS Requirements 3.5.3 and 3.6.3)
- Key generation (PCI DSS Requirement 3.6.1)
- Key distribution (PCI DSS Requirement 3.6.2)
- Rotation / encryption times (PCI DSS Requirement 3.6.4)
- Key exchange (PCI DSS Requirement 3.6.5)
- “Dual control” and “split information” implementation (PCI DSS Requirement 3.6.6)
- Key change prevention (PCI DSS Requirement 3.6.7)
- Retention management (PCI DSS Requirement 3.6.8)
Some of the PCI SSC standards and their HSM system use specifications are described below:
- PCI PIN v3.0 – Requirement 1
- PCI P2PE v3.0 – Requirement 4A-1, 5-1
- PCI 3DS v1.0 – Requirement P2-6.1.2
- PCI Card Production (Logical) v2.0 – Requirement 8.5, 8.7, 8.14
The generation of cryptographic keys also occurs in HSM, which is the only place where unencrypted private or secret keys can be accessed. When a transaction is initiated by a merchant and enters the issuing bank, the cryptographic verification will be executed within the HSM. The full validation verification will also emerge there.
What are the Security Standards for HSMs?
As hardware security modules play a vital role in securing data, there are strict specifications to ensure their effectiveness.
Some of these requirements are Federal Information Processing Standard Publication 140-2 (also known as FIPS 140), which offers third-party verification so that a cryptographic system has minimal power.
FIPS 140 also offers various security features, so not all HSMs are at the same security level and have multiple security degrees to which they comply. The Payment Card Industry Council (PCI) also has its collection of standards for hardware security modules used for payment data.
You can review the PCI HSM requirements from the document below:
Payment Card Industry (PCI) PTS HSM Security Requirements
HSMs come in a variety of sizes and forms. Most HSM is stand-alone devices connected to servers via Ethernet or USB, and some are inserted into the host board through the PCI slot. HSM devices are manufactured by specialist manufacturers and have physical and logical features, depending on the security standard they aim to achieve, such as FIPS or Common Criteria standards.
The level of security offered by HSMs that support PCI DSS is graded using the FIPS 140-2 standard (levels 1 to 4). HSMs compliant with FIPS 140-2 and above security level 3 has the highest protection level. It is equipped with mechanisms that can detect physical intrusions that will cause all highly secure data to be deleted.
Several international standards have been defined to verify the security levels of HSM devices, including:
- FIPS (Federal Information Processing Standard) 140-2 (Security Requirements for Cryptographic Modules): It is a standard aimed at checking the efficacy of cryptographic hardware. Although there is a federal standard in the US and Canada, it is recognized worldwide in both government and private sectors. This certificate defines four levels of security, from the lowest level (Level 1) to the most restrictive (Level 4):
- FIPS 140-2 Level 1: It includes specific security specifications that allow cryptographic module software and firmware components to be executed on a general purpose system using an untested operating system (at least one validated algorithm or function must be used). No physical security mechanisms are included. Example: encryption card of a personal computer.
- FIPS 140-2 Level 2: This level enhances level 1 security by requiring the use of tamper evidence detection and role-based authentication mechanisms. Software applications must be run on a Common Criteria EAL2 certified operating system.
- FIPS 140-2 Level 3: This level requires additional tamper resistance, tamper response, and identity-based authentication. A functional distinction between interfaces from which essential safety parameters enter and exit the device often needs it. Only in encrypted form can private keys be imported or exported.
- FIPS 140-2 Level 4: This last level includes advanced intrusion protection (tamper-active) and is designed for products operating in physically unprotected environments.
- Common Criteria (ISO / IEC 15408): An globally recognised certification level for IT product and device protection is the Common Criteria for Information Technology Security Evaluation. It was developed in the 1990s by Canada, France, Germany, the Netherlands, the UK, and the USA. Common Criteria products are categorized into levels (Evaluation Assurance Level – EAL) with the lowest EAL1 and the most rigorous EAL 7.
- Payment Card Industry (PCI) PTS HSM Security Requirements (PCI HSM): The PCI HSM standard is part of the collection of standards for PCI SSC PIN Transaction Security (PTS) and specifies the necessary security controls during manufacturing, shipping, and usage.
Relevant standards have been developed by some countries, such as Germany, France (CB MEPS), Australia (APCA CECS), or Italy, which may require special certificates for key and algorithm management on HSM devices.
What are the Advantages of Using HSM?
You can encrypt your data without using HSM, but using HSM provides the best approach to theft and data misuse. HSM may be a more costly investment, but it often increases your level of security.
There are many advantages to using an HSM to encrypt data:
- Provides maximum security. HSMs have one of the highest protection requirements against external threats. It is safe to use and helps protect against malicious attacks.
- Take data about customers seriously. It allows you to show customers that you take their privacy seriously by going the extra mile to protect their information, mainly information about their payments.
- You can also take HSM as a service. Some IT providers sell it as a service for companies that cannot afford to invest in HSM but need PCI DSS certification, making this technology more available and suitable for individual businesses.
- Allows you to keep your key in one place. While holding a key in software that can reach almost anywhere, the HSM also has the key, making tracking and protection more straightforward. The switch cannot leave the device.
- You can enjoy tamper-proof defense. HSMs are tamper-proof and are resistant to manipulation due to their specific properties. HSMs offer a degree of protection that is difficult to achieve using software alone.
HSMs provide a secure environment that protects keys throughout their lifecycle and offers healthy controls over who is granted access to keys and what they can do with those keys.
They can ensure that access is granted only when authorized by an administrator and restrict users’ tasks based on their roles. Some users may, for example, be restricted to administrative tasks such as configurations or upgrades; others may be permitted to set or alter the policy, while others may be restricted to the use of unique keys or key sets.
Streamline Your PCI Compliance with HSM
Managing cryptographic keys is the hardest part of cryptography and often the weakest point of a secure system. A secure and not too complicated way to manage cryptographic keys is to use hardware security modules (HSM).
HSM devices allow secure key management, secure processing of sensitive data, and meet stringent security requirements. It is also a safe alternative to the use of standard cryptographic software libraries.
See Also: PCI DSS Key Rotation Requirements
Compared to software solutions, HSMs provide a protected environment isolated from the application host for key generation and data processing. Moreover, HSMs ensure that cryptographic keys are secured when not in use, reducing the attack surface and guarding against unauthorized use of keys.
HSMs can provide digital signature services for various applications. As they are often at the center of an enterprise’s protected infrastructure, they form a holistic defense line against cybercrime. The 3.5.2 Requirement of PCI DSS acknowledges that the use of HSM increases cyber protection.
The use of HSM makes it much easier to meet and audit PCI DSS 3.5.3 and 3.6.1 to 3.6.5 requirements. If HSM technology is implemented correctly, most applications “do as usual” and will help protect all of your sensitive data, not just the PCI DSS areas under review.
If you are serious about maximizing your data protection, it’s essential to combine every device that stores, processes, or tracks data with an HSM. It should be extended to the entire business, not just e-commerce channels as it usually is, but also phone and point-of-sale networks.


